Business Intelligence is a very exiting subject and a field that is undergoing rapid transformation influenced by things such as big data, data visualization, self-service analytics, cloud and mobile computing, etc.
I have published a post titled "Business Intelligence, the Microsoft style" that covered Microsoft's renewed focus on and general strategy around Business Intelligence some time ago. Sure enough, there have been many new and exciting developments related to Microsoft BI since.
So, here are a few things I wanted to include in this update:
I have published a post titled "Business Intelligence, the Microsoft style" that covered Microsoft's renewed focus on and general strategy around Business Intelligence some time ago. Sure enough, there have been many new and exciting developments related to Microsoft BI since.
- Power BI for Office 365 - powerful self-service analytics available as an add-on to Office 365 E3/E4 plans or as a standalone offering
- Microsoft BI at a Glance Poster - pretty good poster that details Microsoft BI components and interactions
- Visio BI -
- Instructional video on Developing Advanced BI Visualizations with Microsoft Visio and SharePoint in the Cloud
- Great article covering Building A Simple BI Dashboard With Visio 2013 And Visio Services
- Microsoft Audit and Control Management (ACM) Server 2013 -
- TechNet reference
- A good blog post the covers Spreadsheet controls in Office 2013
- Another excellent blog post that covers ACM Server 2013
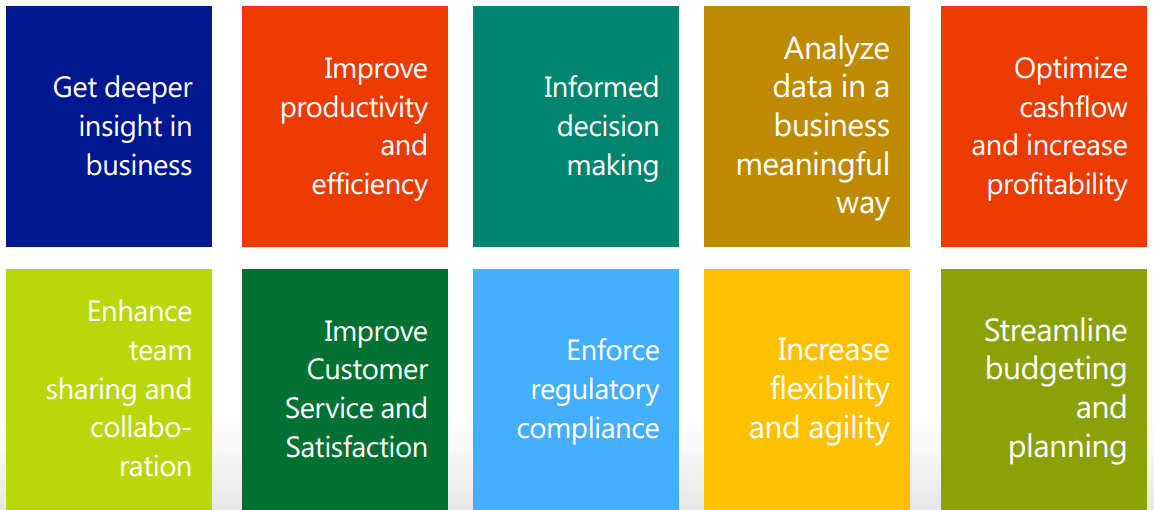
And if you are still wondering - why business intelligence? Here are some of te reasons:

Good Post! Thank you so much for sharing this pretty post, it was so good to read and useful to improve my knowledge as updated one, keep blogging…
ReplyDeleteTableau Online Training
Neither two conquerors could have expanded like they did if it weren't for mobility. Mobility was the key to decisive maneuvering during battle. Varying in size, from 15, 000 to 30, 000 men, each corps was a miniature army headed by a miniature Napoleon.More info
ReplyDeleteHi, Great.. Tutorial is just awesome..It is really helpful for a newbie like me.. I am a regular follower of your blog. Really very informative post you shared here.thanks a lot.
ReplyDeleteC and C++ Training Institute in chennai | C and C++ Training Institute in anna nagar | C and C++ Training Institute in omr | C and C++ Training Institute in porur | C and C++ Training Institute in tambaram | C and C++ Training Institute in velachery